Are you ready for NIS2?
The new NIS2 directive places a whole range of requirements on companies and their cyber security - from minimum measures for cryptography and security procedures for data access to plans for dealing with security incidents. We provide you with an overview and answer the most important questions.

Bad news first: the updated version of the EU Network and Information Security Directive (NIS2 Directive) must be implemented by EU member states by October 17, 2024. Your company should comply with the numerous requirements of NIS2 by then at the latest - otherwise you could face hefty fines. Also, the management will be personally liable for violations of the directive.
The good news: If you are already using security solutions from Microsoft, you and your company may not be missing much to meet the complex requirements. But first things first.
What is NIS2 all about?
Every year, data security incidents cause massive economic damage. Attacks on companies are becoming more frequent, more complex and therefore more dangerous. At the same time, networks are becoming more vulnerable in view of remote working and business activities in an increasingly connected world. This is where NIS2 comes in.
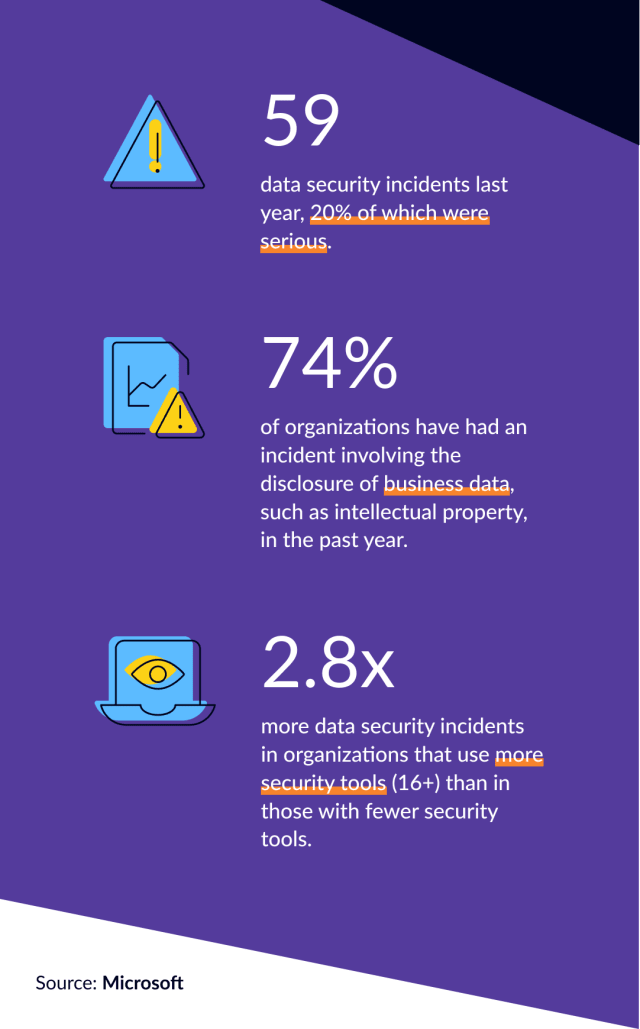
The aim of the European directive is to harmonize the requirements for modern cybersecurity and its enforcement in the EU member states by setting a benchmark for minimum measures that companies must meet. NIS2 will thus be the most comprehensive European cybersecurity directive, covering 18 sectors.
Each country must transpose the directive into national law by October 2024, leaving room for national specifics. However, there are some minimum requirements that must be implemented in any case. As many countries currently (as of April 21, 2024) have no official draft legislation for the implementation of NIS2, it is not exactly easy for companies to prepare for the new directive. However, some important questions can already be answered.
Is NIS2 relevant for you?
First of all, you should make sure that the NIS2 directive applies to you and your organization. This check does not happen automatically but must be carried out independently by companies. NIS2 divides companies into “essential” and “important” categories, some of which differ in terms of requirements. Also, the size and turnover of each organization plays a role in defining which criteria apply. This affects 18 sectors in total:
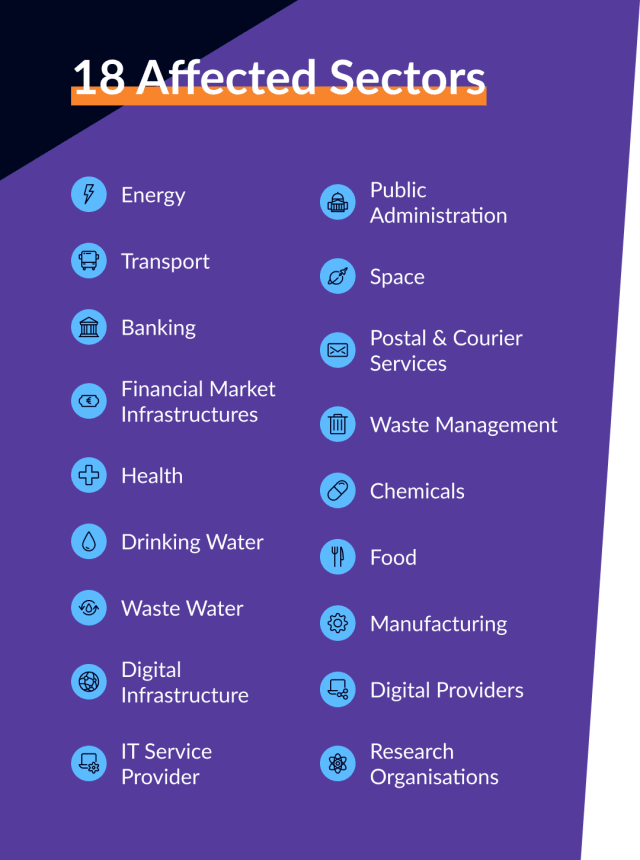
Please note: NIS2 affects the entire supply chain of a company. Therefore, the directive may apply to you even if you do not meet the respective criteria but are part of the supply chain of a company affected by NIS2.
What are the requirements of NIS2?
NIS2 builds on previous legislation such as NIS1 and GDPR but adds numerous new requirements. The details of these new requirements will not be clear until a final draft of the legislation is published, but companies can already make comprehensive preparations now.
This is because NIS2 compliance is aligned with the same Zero Trust principles that Microsoft security solutions already take into account in order to provide solid protection against cyberattacks across the entire attack surface.
The policy is based on a number of principles that can be ensured either with Microsoft solutions or our services and products. We have summarized the most important principles here:
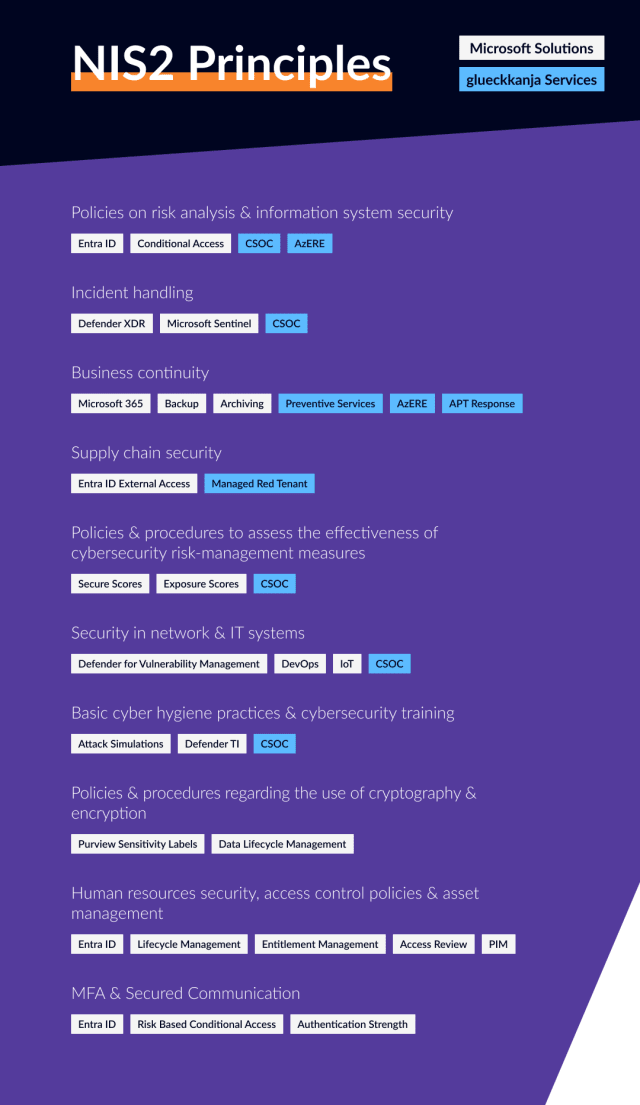
What can companies do now?
With October approaching and the draft legislation still pending in many countries, it may be tempting for companies to speculate on possible grace periods from the government. However, the switch to NSI2-compliant systems can have potentially far-reaching consequences which need to be thoroughly planned, especially for organizations still working with legacy solutions.
Our clear recommendation is therefore not to wait any longer and to act now. Even before the NIS2 directive comes into effect, your organization will benefit from a solid risk management strategy, timely incident reporting, the ability to audit the supply chain and maintain a complete inventory of all digital assets.
We can support you not only in managing existing Microsoft security solutions, but also in setting up additional protection mechanisms. Our specialized Cloud Security Operations Center (CSOC), which is closely integrated with Microsoft security technologies, makes it possible to efficiently monitor and evaluate alerts, distinguish real threats from false positives and thus ensure comprehensive protection against digital threats. By integrating additional data sources (non-Microsoft data sources) and using advanced tools such as Microsoft Sentinel, we offer standardized security solutions that are precisely tailored to the specific needs of each customer.
